GNU Radio – CC1111 packets encoder/decoder blocks
Introduction
I recently worked with RF transmissions between CC1111-based devices (the chips that are supported by RFCat) and I was in the need to easily encode and decode my payloads using GNU Radio. GNU Radio already contains several packets encoder/decoder blocks, but none of them (if I’m right, and I hope that I am) deal with the same header length, whitening algorithm and/or checksum used by the CC1111 chips. In the CC1111 world, the header is one byte length, the checksum is CRC16 and the data whitening is performed using the following algorithm http://www.ti.com/lit/an/swra322/swra322.pdf.
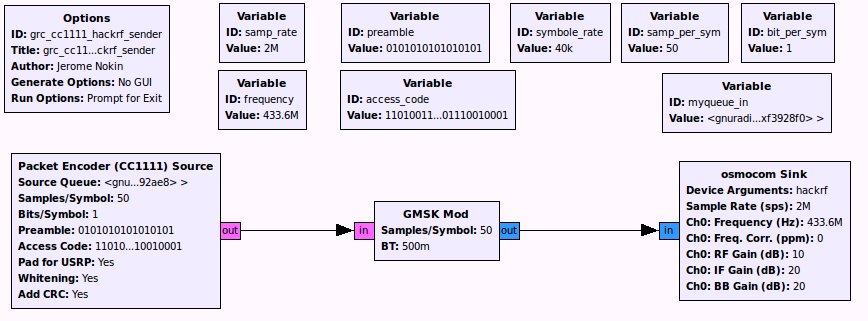
Packet encoder
Here is a simple GRC flow-graph demonstrating how to encode and transmit CC1111 packets using your favorite SDR device:
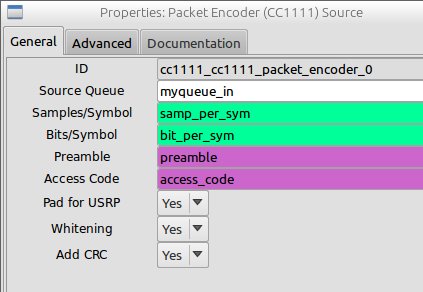
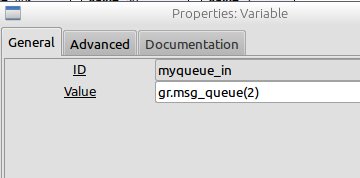
As you can see, the Source block accepts a Source Queue argument defined like this:
Using this flow-graph, it is then easy to transmit new CC1111 packets from any other python scripts, just by tailing new payload into the “myqueue_in” message queue. Example:
#!/usr/bin/python
import sys
from gnuradio import gr
import grc_cc1111_hackrf_sender
rf = grc_cc1111_hackrf_sender.grc_cc1111_hackrf_sender()
rf.set_frequency(long(sys.argv[1]))
rf.start()
msg = gr.message_from_string("Hello from HackRF One")
rf.myqueue_in.insert_tail(msg)
sys.exit(0)
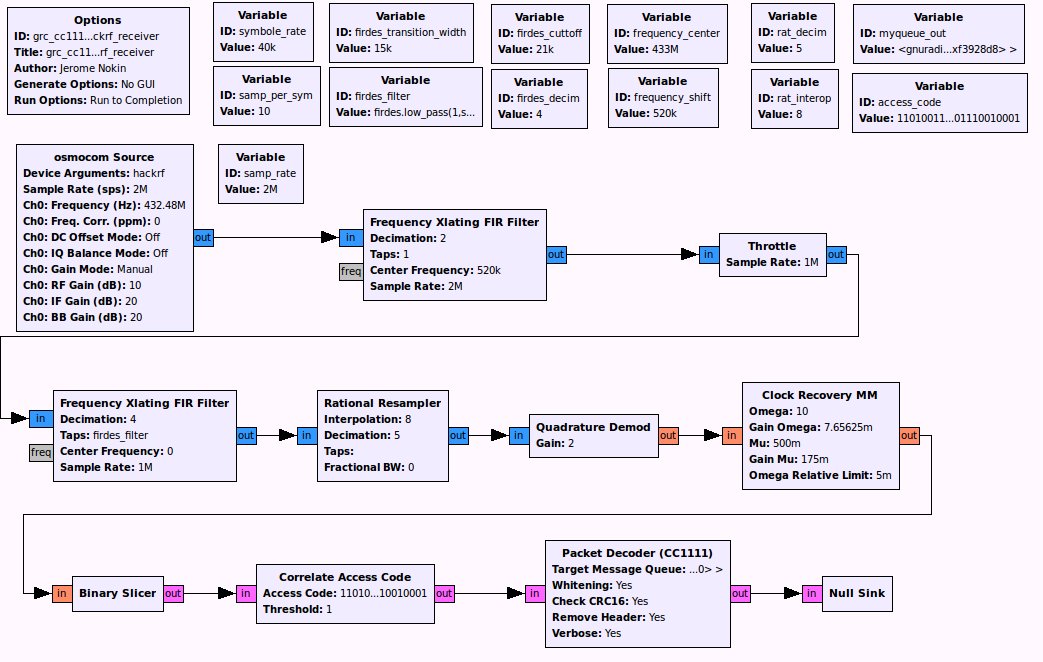
Packet Decoder
In the other sense, the following GRC flow-graph can be used to demodulate a 2FSK modulated signal (transmitted for example by RFCat), and to decode the CC1111 formated packets.
Here again, the decoder block accepts a message queue as argument (Target Message Queue = myqueue_out), that you can then access from your python script:
#!/usr/bin/python import sys from gnuradio import gr import grc_cc1111_hackrf_receiver freq = long(sys.argv[1]) rf = grc_cc1111_hackrf_receiver.grc_cc1111_hackrf_receiver() rf.set_frequency_center(freq) rf.start() msg = rf.myqueue_out.delete_head().to_string() print "[hackrf rcv] : '%s'" % msg sys.exit(0)
Download and install
While these new blocks are still considered as beta, tests were performed between RFCat, RTL-SDR and the HackRF One with good success rate. You will find multiple testing scripts in the repository, ready to handle RF transmissions between RFCat and GNU Radio (see “testing-scripts” folder).
Get the source from: https://github.com/funoverip/gr-cc1111
git clone https://github.com/funoverip/gr-cc1111.git cd gr-cc1111/src/gr-cc1111/ mkdir build cd build cmake ../ make sudo make install
Enjoy.
© 2014, foip. All rights reserved.

 (10 votes, average: 4.30 out of 5)
(10 votes, average: 4.30 out of 5)
First of all thanks for the post i didn’t imagine that such blog exist until i was checking my “forgotten files” and i found ultimate-payload-v0.1/ (nice tool) and i follow the link and her i’am navigating in this wonderfull blog (keep up the hard work man)
For GNU radio i hope that i can afford bying the device there are some realy realy good usage of it
Thanks
Hello! This is awesome stuff and happens to be very useful to me. My own attempts to process CC1111 packets went to dead end. These blocks are the missing piece! Thank you!