McAfee SiteList.xml password decryption
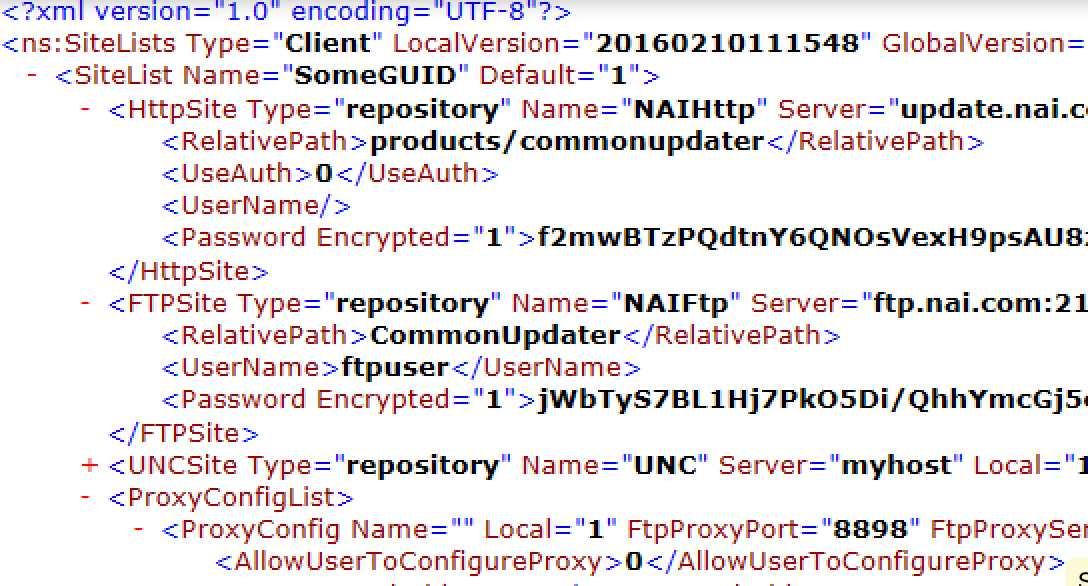
Recently, a very good friend of mine (@Sn0rkY) pointed me out the story of a pentester who recovered the encrypted passwords from a McAfee SiteList.xml file, using Responder (link). Simply clever.
Since I worked hard on McAfee products in the past (see ePolicy 0wner), he asked me if I knew how to decrypt these passwords, directly from the SiteList.xml file. The answer was no. But, another link from SySS GmbH pointed out that the encryption was based on 3DES and some XOR. What ?!? That sounds very similar to what I’ve found earlier in ePolicy Orchestrator !
So, back into IDA Pro and Immunity Debugger, I’ve found that – indeed – the algorithm reused the same hardcoded 3DES key in ECB mode, but that the XOR was a bit different. A short python implementation of the reversed algorithm provided me with the following result:
$ ./mcafee_sitelist_pwd_decrypt.py 'jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q==' Crypted password : jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q== Decrypted password : MyStrongPassword!
Yes ! :-)
It is time to share this knowledge with the penetration testing community. Isn’t ?
https://github.com/funoverip/mcafee-sitelist-pwd-decryption
Happy password recovering!
foip
© 2016 – 2022, foip. All rights reserved.
Comments are closed.


 (12 votes, average: 3.58 out of 5)
(12 votes, average: 3.58 out of 5)
You’re alive! I was starting to think Verisure had sent goons after you. ;-)
Verisure sure took his life :)
He knows as well as all others that his last comment at part 2 is total nonsense.
Prob brought because things got to hot under his feet :)